Credit: Hanacek / NIST
We can create software with 100 times fewer vulnerabilities than we do today, according to computer scientists at the National Institute of Standards and Technology (NIST). To get there, they recommend that coders adopt the approaches they have compiled in a new publication.
The 60-page document, NIST Interagency Report (NISTIR) 8151: Dramatically Reducing Software Vulnerabilities (link is external), is a collection of the newest strategies gathered from across industry and other sources for reducing bugs in software. While the report is officially a response to a request for methods from the White House's Office of Science and Technology Policy, NIST computer scientist Paul E. Black says its contents will help any organization that seeks to author high-quality, low-defect computer code.
"We want coders to know about it," said Black, one of the publication's coauthors. "We concentrated on including novel ideas that they may not have heard about already."
Black and his NIST colleagues compiled these ideas while working with software assurance experts from many private companies in the computer industry as well as several government agencies that generate a good deal of code, including the Department of Defense and NASA. The resulting document reflects their cumulative input and experience.
Vulnerabilities are common in software. Even small applications have hundreds of bugs (link is external) by some estimates. Lowering these numbers would bring many advantages, such as reducing the number of computer crashes and reboots users need to deal with, not to mention decreasing the number of patch updates they need to download.
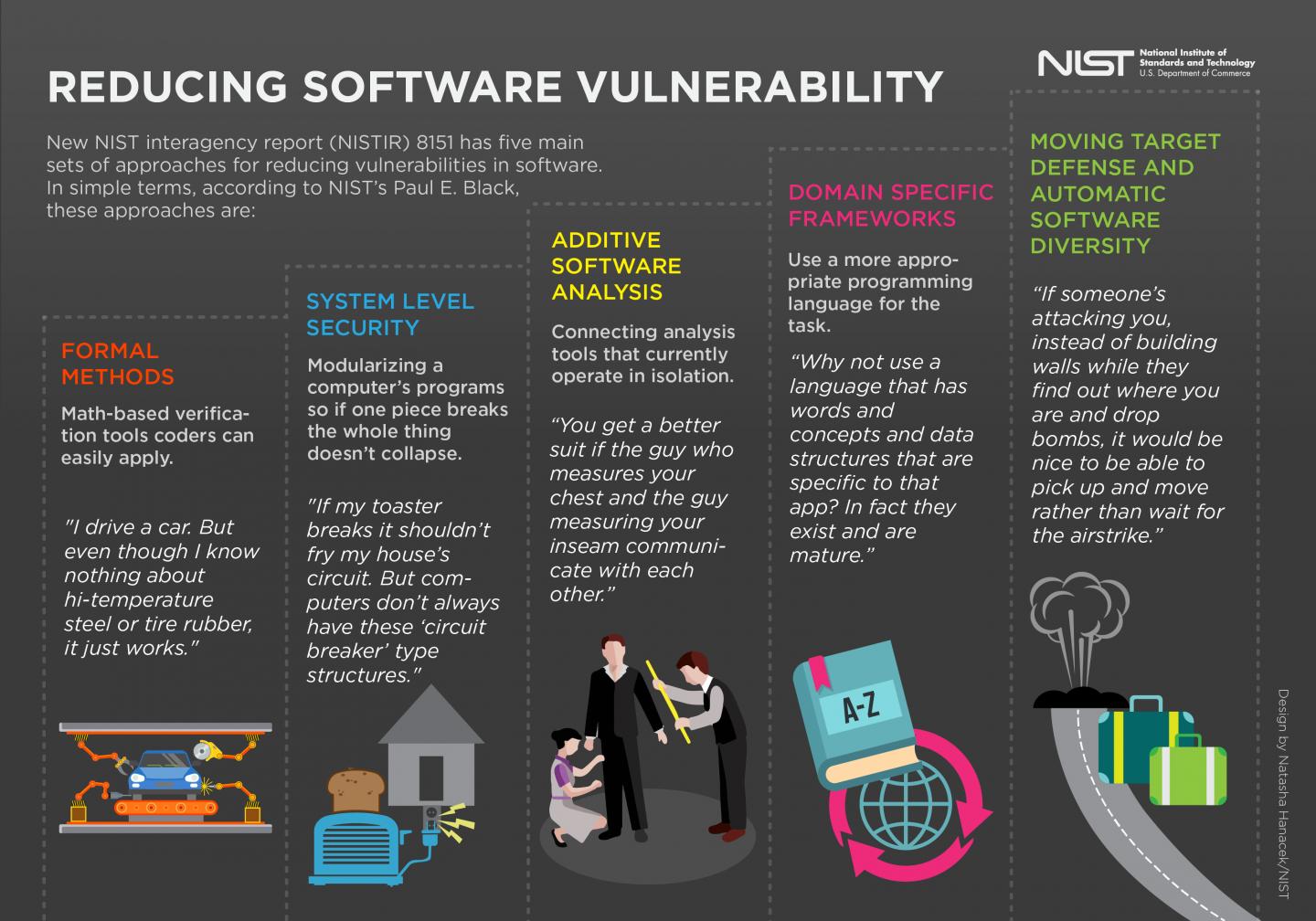
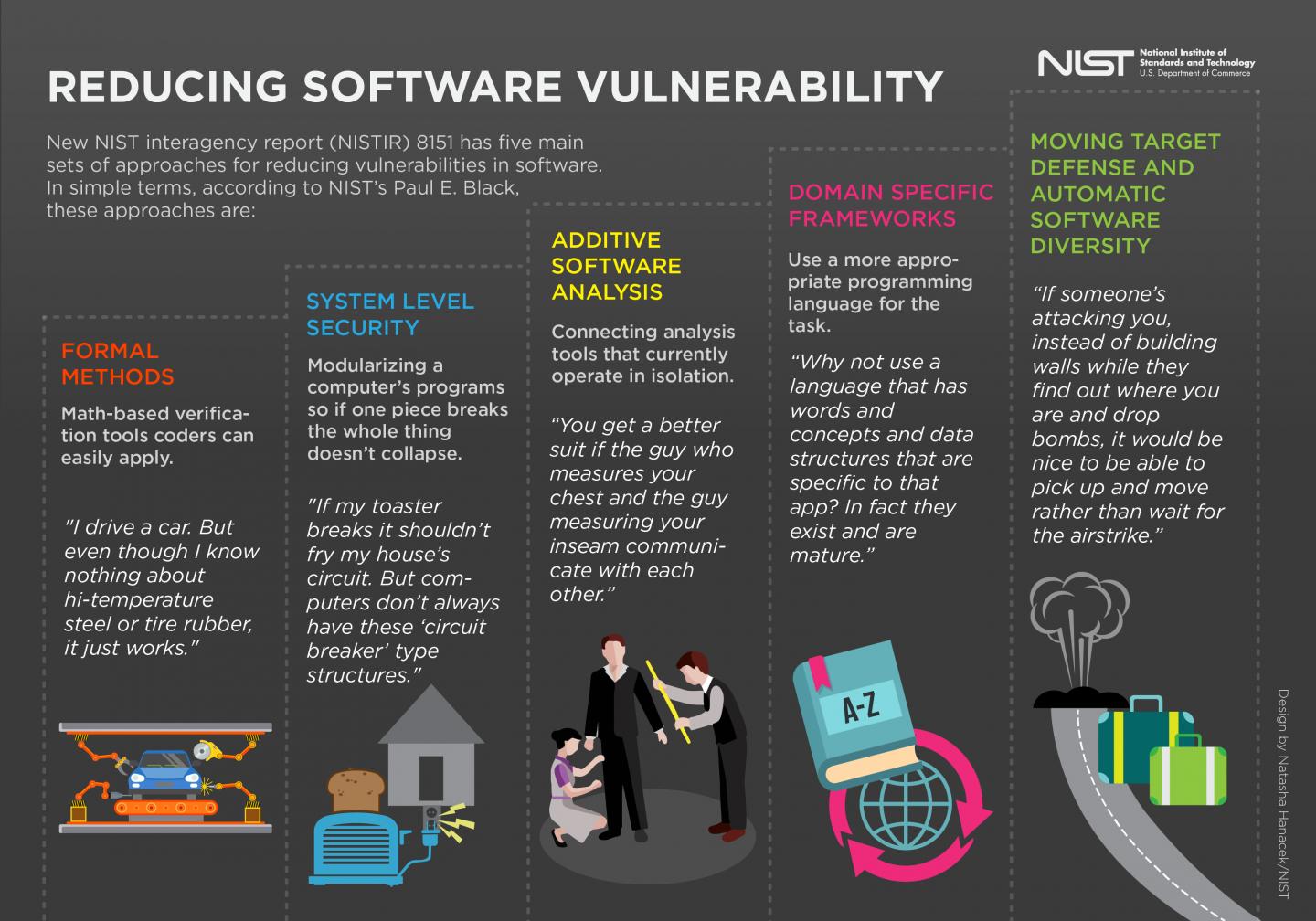
The heart of the document, Black said, is five sets of approaches, tools and concepts that can help, all of which can be found in the document's second section. The approaches are organized under five subheadings that, despite their jargon-heavy titles, each possess a common-sense idea as an overarching principle (see downloadable infographic).
These approaches include: using math-based tools to verify the code will work properly; breaking up a computer's programs into modular parts so that if one part fails, the whole program doesn't crash; connecting analysis tools for code that currently operate in isolation; using appropriate programming languages for the task that the code attempts to carry out; and developing evolving and changing tactics for protecting code that is the target of cyberattacks.
In addition to the techniques themselves, the publication offers recommendations for how the programming community can educate itself about where and how to use them. It also suggests that customers should request the techniques be used in development. "You as a consumer should be able to write it into a contract that you want a vendor to develop software in accordance with these principles, so that it's as secure as it can be," Black said.
Security is, of course, a major concern for almost everyone who uses technology these days, and Black said that the White House's original request for these approaches was part of its 2016 Federal Cybersecurity R&D Strategic Action Plan, intended to be implemented over the next three to seven years. But though ideas of security permeate the document, Black said the strategies have an even broader intent.
"Security tends to bubble to the surface because we've got adversaries who want to exploit weaknesses," he said, "but we'd still want to avoid bugs even without this threat. The effort to stymie them brings up general principles. You'll notice the title doesn't have the word 'security' in it anywhere."
###
Media Contact
Chad Boutin
[email protected]
301-975-4261
@usnistgov
http://www.nist.gov
############
Story Source: Materials provided by Scienmag