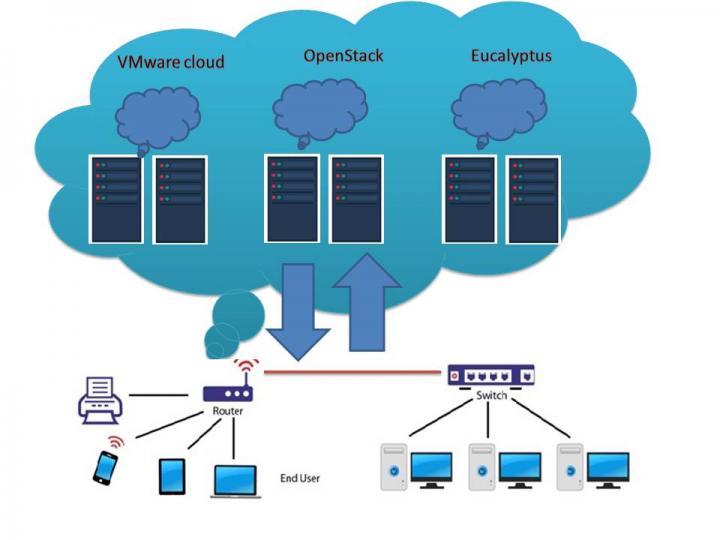
The central goal of cloud computing is to provide fast, easy-to-use computing and data storage services at a low cost. However, the cloud environment comes with data confidentiality risks attached.
Cryptography is the primary tool used to enhance the security of cloud computing. This mathematical technique protects the stored or transmitted data by encrypting it, so that it can only be understood by intended recipients. While there are many different encryption techniques, none are completely secure, and the search continues for new technologies that can counter the rising threats to data privacy and security.
In a recent study published in KeAi’s International Journal of Intelligent Networks, a team of researchers from India and Yemen describe a novel, two-step cryptography technique – the first to combine genetic technology with mathematical technique. According to the paper’s authors, it generates a complex cryptographic environment with high security and flexibility that could spark a paradigm shift in data confidentiality.
The paper’s corresponding author, Fursan Thabit of Swami Ramanand Teerth Marathwada University in India, explains: “Some existing famous ciphers use the Feistel structure for encryption and decryption. Others use the Network SP (Substitution-Permutation). The first level of our encryption uses a logical-mathematical function inspired by a combination of the two. Not only does it improve the complexity of the encryption, it also increases energy efficiency by reducing the number of encryption rounds required.”
The researchers’ second encryption layer is inspired by structures of genetics techniques based on the Central Dogma of Molecular Biology (CDMB). It simulates the natural processes of genetic coding (translation from binary to DNA bases), transcription (regeneration from DNA to mRNA), and translation (regeneration from mRNA to protein).
Thabit adds: “We are the first to mix the DNA, RNA and genetics techniques for a cryptographic purpose and the first to combine the technique of genetic encryption with mathematics to generate a complex key.”
The researchers evaluated the robustness of their new algorithm by measuring encryption time, decryption time, throughput and the length of the cipher-text produced. They found that compared with other genetics encryption techniques and existing symmetric key encryption techniques, their proposed algorithm has high-security strength and is very flexible. It also requires relatively less time than other techniques. In addition, computational and processing strength complexity is reduced due to the algorithm’s clear structure – two layers of encryption containing only four rounds of coding.
Thabit explains: “That clear structure means each round requires only simple math and a genetics simulation process.”
He adds: “We found our proposed encryption scheme is safe for brute force, known plain-text attacks, encrypted text only, and differential cryptanalysis attacks. It has been tested on various data, including whitespace and special characters and it meets the CIA’s principle (Confidentiality, Data integrity, Availability).”
###
Contact the corresponding author: Fursan Thabit, [email protected] (Twitter: https:/
The publisher KeAi was established by Elsevier and China Science Publishing & Media Ltd to unfold quality research globally. In 2013, our focus shifted to open access publishing. We now proudly publish more than 100 world-class, open access, English language journals, spanning all scientific disciplines. Many of these are titles we publish in partnership with prestigious societies and academic institutions, such as the National Natural Science Foundation of China (NSFC).
Media Contact
Cassie He
[email protected]
Related Journal Article
http://dx.