Purdue innovators are at Silicon Valley’s premier chip-design conference to unveil technology that is 100 times more resilient to electromagnetic attacks to secure Internet of Things devices
Credit: Shreyas Sen/Purdue University
WEST LAFAYETTE, Ind. – Security of embedded devices is essential in today’s internet-connected world. Security is typically guaranteed mathematically using a small secret key to encrypt the private messages.
When these computationally secure encryption algorithms are implemented on a physical hardware, they leak critical side-channel information in the form of power consumption or electromagnetic radiation. Now, Purdue University innovators have developed technology to kill the problem at the source itself – tackling physical-layer vulnerabilities with physical-layer solutions.
Recent attacks have shown that such side-channel attacks can happen in just a few minutes from a short distance away. Recently, these attacks were used in the counterfeiting of e-cigarette batteries by stealing the secret encryption keys from authentic batteries to gain market share.
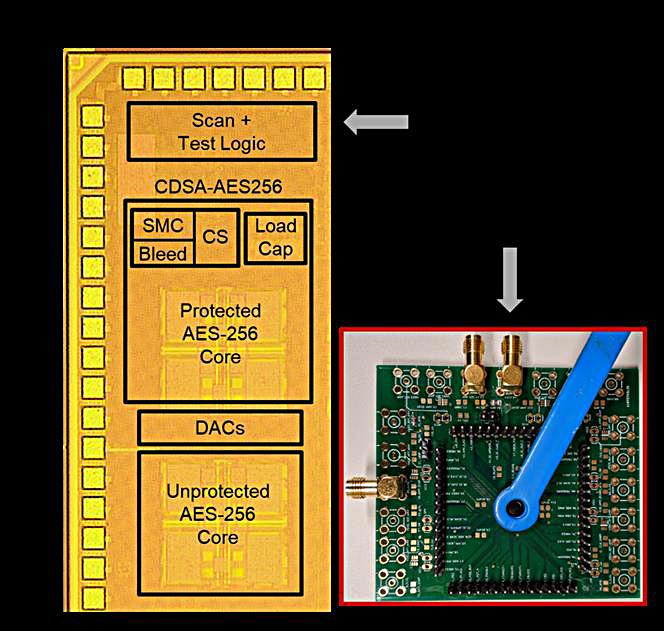
“This leakage is inevitable as it is created due to the accelerating and decelerating electrons, which are at the core of today’s digital circuits performing the encryption operations,” said Debayan Das, a Ph.D. student in Purdue’s College of Engineering. “Such attacks are becoming a significant threat to resource-constrained edge devices that use symmetric key encryption with a relatively static secret key like smart cards. Our technology has been shown to be 100 times more resilient to these attacks against Internet of Things devices than current solutions.”
Das is a member of Purdue’s SparcLab team, directed by Shreyas Sen, an assistant professor of electrical and computer engineering. The team developed technology to use mixed-signal circuits to embed the crypto core within a signature attenuation hardware with lower-level metal routing, such that the critical signature is suppressed even before it reaches the higher-level metal layers and the supply pin. Das said this drastically reduces electromagnetic and power information leakage.
“Our technique basically makes an attack impractical in many situations,” Das said. “Our protection mechanism is generic enough that it can be applied to any cryptographic engine to improve side-channel security.”
###
A paper the team prepared in collaboration with Intel Corp. and the Georgia Institute of Technology will be presented this week at the International Solid-States Circuit Conference, the world’s premier integrated circuit design conference.
A short video demonstration of this mixed-signal ASIC is available at https:/
The National Science Foundation funded part of the research for the Purdue team.
Sen and his team regularly work with the Purdue Research Foundation Office of Technology Commercialization to patent their technologies. The office recently moved into the Convergence Center for Innovation and Collaboration in Discovery Park District, located on the west side of the Purdue campus.
About Purdue Research Foundation Office of Technology Commercialization
The Purdue Research Foundation Office of Technology Commercialization operates one of the most comprehensive technology transfer programs among leading research universities in the U.S. Services provided by this office support the economic development initiatives of Purdue University and benefit the university’s academic activities through commercializing, licensing and protecting Purdue intellectual property. The office is managed by the Purdue Research Foundation, which received the 2019 Innovation and Economic Prosperity Universities Award for Place from the Association of Public and Land-grant Universities. The Purdue Research Foundation is a private, nonprofit foundation created to advance the mission of Purdue University. Visit the Office of Technology Commercialization for more information or contact [email protected].
Writer: Chris Adam, 765-588-3341, [email protected]
Sources: Shreyas Sen, [email protected]
Debayan Das, [email protected]
Paper: 27.3: EM and Power SCA-Resilient AES-256 in 65nm CMOS Through >350× Current-Domain Signature Attenuation
Media Contact
Chris Adam
[email protected]




